LANmapper - PCI:DSS Compliance

This page will describe how using LANmapper it is possible to understand your network traffic like never before, and use this knowledge to build a secure and consise firewall rulebase.
Company Overview
Founded in 2010 by Dan McGrath, Activ8 Information Security (www.activ8is.com) is a versatile and progressive consultancy that is independently owned and operated.Based in Bristol, UK, the team is focused on creating original security-centric software designed for all major platforms (and also some not-so-major ones.)
 Our security solutions are used in the most demanding network environments, and are built to the very highest standards.
Our security solutions are used in the most demanding network environments, and are built to the very highest standards.
LANmapper
Lanmapper was written to address a request raised by a customer for our other product LANreveal (www.lanreveal.com) to produce more detailed and automated diagramming.You can rely on LANmapper (and it's sister product LANreveal) to prevent cyber threats, reduce risk exposure and demonstrate network compliance with regulations such as PCI:DSS, ISO27001, Sarbanes Oxley (SOX) etc...
Where to start?
Security is exceptionally important to all of our customers.However, due to rapid growth, changes in staff, limited documentation etc.. it is often the case that companies are left wondering exactly what is going on with their network. This can make firewall configuration extremely tricky and may cause isses at audit time (PCI, ISO27001, SOX etc..)
Do your Comms-Rooms and Data-Centres look like this?...
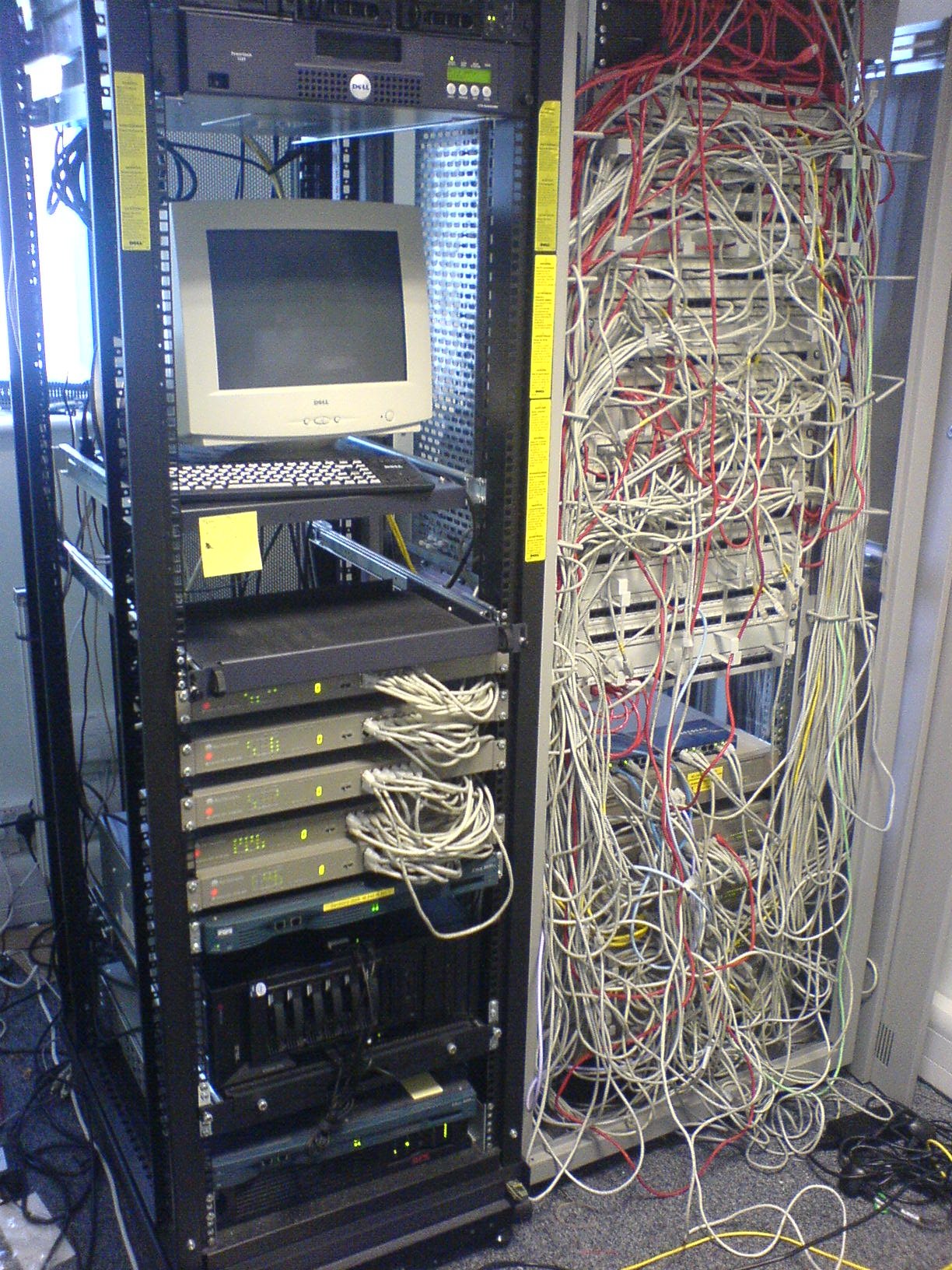 Using LANmapper is a simple way to regain control of your firewalls, and acurately understand exactly what is happening on your network today.
Using our revolutionary technology, LANmapper can help you to understand your network, help you understand how business processes map to network traffic and ultimatly help you to protect your enterprise accordingly.
Using LANmapper is a simple way to regain control of your firewalls, and acurately understand exactly what is happening on your network today.
Using our revolutionary technology, LANmapper can help you to understand your network, help you understand how business processes map to network traffic and ultimatly help you to protect your enterprise accordingly.
Here is what Simon Hoscik (Senior Security Analyst at Virgin Mobile) had to say about LANmapper:
Simon Hoscik“ Without a doubt, deployment of LANmapper has been of significant benefit to Virgin Mobile. As a direct result of using LANmapper we were quickly able to visualise and understand the entire network traffic interconnection profile of our enterprise. Having this knowledge has allowed us to build a PCI compliant firewall configuration. ”
Senior Security Analyst,
Virgin Mobile
How does it work?
LANmapper is an agent based network discovery application.We have agents available for almost all operating systems (including MS Windows, Solaris, HPUX, AIX, Linux and more)
These agents are written in a number of different languages depending on the host operating system, but in all cases are humanly readable script - not invisible compiled code, meaning that you are able to see clearly what the agent is doing.
The agents are left to collect data for a period of time (normally around a month) after which time the resulting data is collected and processed off-site using our bespoke engine software.
 Off-site processing is used for a number of reasons, the main being that the agents (by design) have very-very low cpu and resource requirements, which ensures that using LANmapper won't interfere with your day-to-day business operations.
Off-site processing is used for a number of reasons, the main being that the agents (by design) have very-very low cpu and resource requirements, which ensures that using LANmapper won't interfere with your day-to-day business operations.
Processing the resulting data, however is exceptionally processor intensive and so we conduct this off-site using our bespoke and purpose built processing facility.
Once the data has been collected and processed, it can be represented in many different ways - some examples of which are given below.
This is an example of LANmapper output for a sinlge host connectivity. In the diagram below, the host 'ERPSVR' is the host of interest, this diagram shows all connectivity to and from this server.
Network Documentation
The simplest form being simply a text file containing information on the observed connections, along with their relative frequency: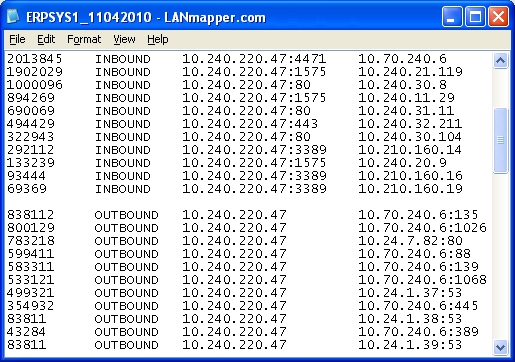
Network Spreadsheets
Alternatively this information can be automatically imported into MS Excel or rendered as an Adobe Acrobat file - possibly for inclusion into a report.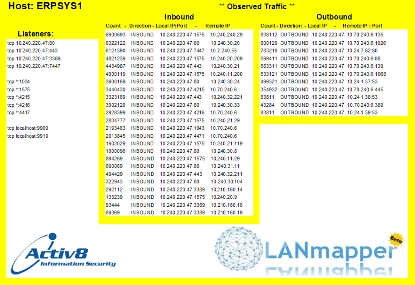
View as HTML map | View as PDF file
Network Diagrams
If you'd like to actually SEE the information, then graphical representations can be created. Host-centric DiagramsEither on a host by host basis, with a single diagram with each host at the centre. Click on the images to see larger versions.
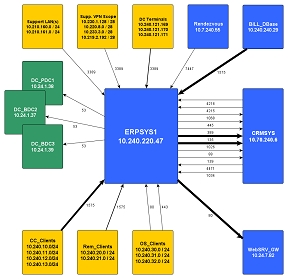
View as HTML map | View as PDF file | View as Flash diagram
A few points to note:1) Line thickness is proportional to traffic frequency (configurable)
2) Box size is proportional to traffic volumes.
3) All ports are TCP unless stated otherwise.
4) Colours are used to represent different subnets (however colour can be used to represent environments, domains etc..)
Enterprise Diagrams
Alternatively, several hosts can be combined into one larger diagram showing all interconnection between key hosts and also any number of external systems. These diagrams can be as simple or as complex as you require. To-date we've analysed systems with as few a 5 servers, or as many as 150.
The example below is a simple illustration of this:
Click on the images to see larger versions.
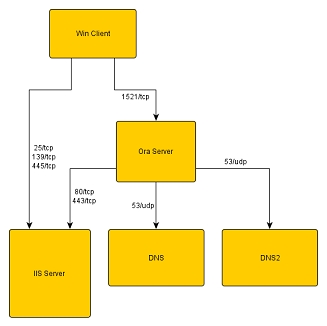
View as HTML map | View as PDF file| View as Flash diagram
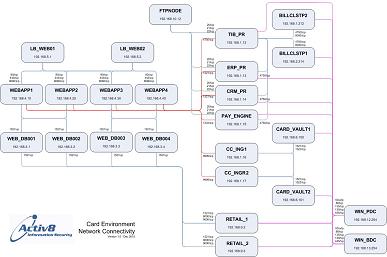
This diagram is a representation of an entire card processing environment for a major on-line retailer.Click on the images to see larger versions.
Below is a diagram depicting a number of key systems involved in a large warehousing / ERP system.
Click on the images to see larger versions.
View as HTML map | View as PDF file| View as Flash diagram
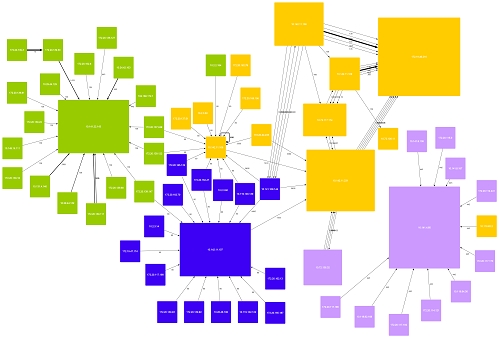
This digram uses colour to great effect, orange is used to represent the in-scope system, with green used for all systems which directly connect to the orange (in-scope) system, and then blue is used for all systems which interface with the green.In this case, the different colours represent the different degrees of separation between hosts.
Click on the images to see larger versions.
View as HTML map | View as PDF file| View as Flash diagram
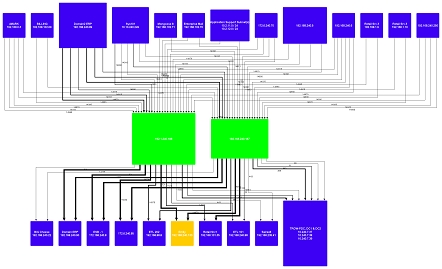
Finally a large intranet installation. Again colour is used, but in this case it depicts different types of clients. For example orange is used to highlight the webclients (http - port 80)Click on the images to see larger versions.
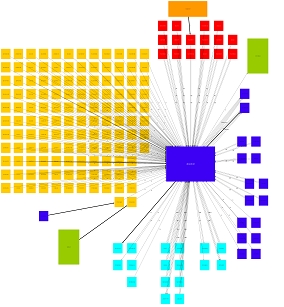
View as HTML map | View as PDF file| View as Flash diagram
Firewall Config Files
Finally, we can take the information above, and use it to actually (and automatically) generate your firewall rules: This can result in any or all of the following.access-list inbound permit tcp host 10.240.220.47 10.240.31.0 255.255.255.0 eq http
access-list inbound permit tcp host 10.240.220.47 10.240.32.0 255.255.255.0 eq http
access-list inbound permit tcp host 10.240.220.47 10.240.30.0 255.255.255.0 eq https
access-list inbound permit tcp host 10.240.220.47 10.240.31.0 255.255.255.0 eq https
access-list inbound permit tcp host 10.240.220.47 10.240.32.0 255.255.255.0 eq https
access-list inbound permit tcp host 10.240.220.47 10.240.20.0 255.255.255.0 eq sql
access-list inbound permit tcp host 10.240.220.47 10.240.21.0 255.255.255.0 eq sql
access-list inbound permit tcp host 10.240.220.47 10.240.160.0 255.255.255.0 eq rdp
access-list inbound permit tcp host 10.240.220.47 10.240.161.0 255.255.255.0 eq rdp
access-list inbound permit tcp host 10.240.220.47 10.240.121.169 255.255.255.252 eq rdp
access-list inbound permit ip 10.240.220.47 255.255.255.0 host 10.38.6.236
access-list inbound permit tcp host 10.240.220.47 host 10.240.240.29 eq 1575
access-list outbound permit tcp host 10.70.240.6 host 10.240.220.47 eq 135
access-list outbound permit tcp host 10.70.240.6 host 10.240.220.47 eq 1026
access-list outbound permit tcp host 10.70.240.6 host 10.240.220.47 eq kerberos
access-list outbound permit tcp host 10.70.240.6 host 10.240.220.47 eq 139
access-list outbound permit tcp host 10.70.240.6 host 10.240.220.47 eq 1068
access-list outbound permit tcp host 10.70.240.6 host 10.240.220.47 eq 445
access-list outbound permit tcp host 10.70.240.6 host 10.240.220.47 eq 389
access-list outbound permit ip host 10.70.1.37 host 10.240.220.47 eq domain
access-list outbound permit ip host 10.70.1.38 host 10.240.220.47 eq domain
access-list outbound permit ip host 10.70.1.39 host 10.240.220.47 eq domain
access-list outbound permit tcp host 10.24.7.82 host 10.240.220.47 eq http
access-list inbound deny ip any any
access-list outbound deny ip any any

